

Protect your enterprise with IoT
remediation and repatriation at scale

The only enterprise IoT security platform that can remediate and repatriate all your IoT devices.

Reduce your attack surface with
authorized, authenticated, and
monitored IoT devices
The Viakoo Action Platform helps cyber security teams keep their enterprises operating and safe.














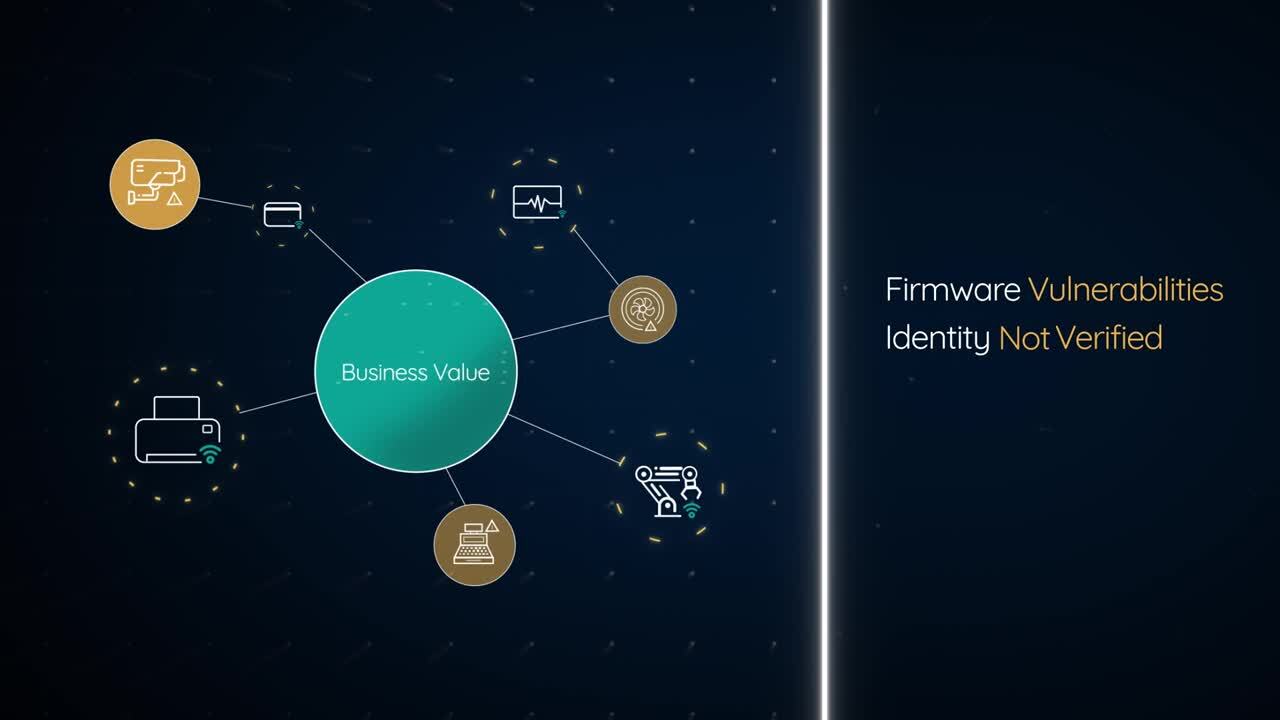
Fully manage cyber hygiene and IoT security performance across virtually any number of distributed enterprise IoT devices and systems from any vendor from anywhere from a single browser-based console.
Nearly 75% of all IoT security problems can be fixed remotely via Viakoo’s easy-to-use-interface, which accelerates time-to-fix by pinpointing operations and IoT security risk. Viakoo finds IoT devices that are out-of-compliance with firmware, have old passwords, or use out of date security certificates.
Discover, update, monitor, and fix all your enterprise IoT security without lifting a finger. Reduce cost while reducing the enterprise risks with automated, controlled system-wide updates.


Armis provides visibility into all enterprise IoT devices on your network, regardless of whether they are managed or unmanaged. This allows you to identify potential risks quickly and take steps to mitigate them. The Viakoo Action Platform helps you remediate risks by taking action to fix vulnerabilities. This prevents cyber attackers from exploiting weaknesses in your enterprise IoT devices and helps to keep your organization safe.

The need for the combined discovery & end-to-end remediation for your enterprise IOT security platform has never more important!
Current estimates show typically there are approximately 5-10 IoT devices per full-time employee, or thousands in an enterprise, put to work solving business problems and delivering critical services to the organization.
The Viakoo Action Platform debuted in October to deliver remediation and repatriation of IoT devices, enabling them to join or rejoin as a full citizen with an audit trail for governance and compliance.
The Viakoo security platform automatically discovers, monitors, and updates IoT device firmware, passwords, and network SSL certificates for unlimited devices across an enterprise.



Viakoo, Inc.
650 Castro St. Suite 120-203
Mountain View, CA 94041
(650) 263-8225
[email protected]
Support
Phone: (650)263-8225
Email: [email protected]
Get the Latest from Viakoo
© 2023 Viakoo Inc All rights reserved.